Recover an ‘assumed bricked’ Vera Secure
-
Looks a nice set up..
Oh, you’ve just reminded me, I use my QNAP as a NVR too (6 cameras), plus I also have ‘ sonos-http-api’ running (using Joanna), and PiHole’ too.
Connectivity wise, I use my UniFi home set up for VPN, and it has 3 networks, (I) Private LAN, (ii) Guest (Internet Only) for visitors & IoT devices (Alexa/Ring etc) and (iii) Video (IP TV) - I’d really like to embed my UniFi controller into my HA much more, as it has a lot of useful info, energy usage (via PoE), presence awareness via access points. Currently I just do some json calls here and there.
-
Hi @rafale77
There was some interesting developments on the Vera forum about recovering a veraplus, through connecting a USB to TTY device to some connectors on the board . Opening up the unit and looking at the VeraSecure board, I can see 4 connectors too. (Photo posted on that forum) https://community.ezlo.com/t/can-the-veraplus-be-unbricked/204485/34
Is that a route you’ve used before ?
-
Not really. The route used before was using a custom windows tool from vera designed for the vera3 which I believe to start a TFTP server which then injects a firmware image to the device over ethernet. This would be something new (well sort of since I think someone on the forum also used TTY to recover one unit as well but not through USB.)
-
Thanks,
While I’ve got the vera3 program somewhere, although as yet I’ve not been able to get it to install/run, having built an XP machine just for that purpose..
it’s interesting you talk about a TFTP server, as I had to do a recovery with a different product, and they sent me instructions on setting up a DHCP server and a TFTP service all using tftd32/64 - http://tftpd32.jounin.net/tftpd32_download.html
I’ve also seen these..
And then for the cable/connection..
Assuming I can get to the command line via putty and the usb-tty cable on Vera; any idea what the sequence and command line(s) might be download and run the firmware update ?
-
-
Yup! These are the two known methods to write the flash memory of an embedded device (TFTP and TTY). I don’t have a vera secure and have only recovered vera plus and vera edge through TFTP. Sorry can’t help with the TTY USB as have taken down my veras.
@rafale77 said in Recover an ‘assumed bricked’ Vera Secure:
Yup! These are the two known methods to write the flash memory of an embedded device (TFTP and TTY). I don’t have a vera secure and have only recovered vera plus and vera edge through TFTP. Sorry can’t help with the TTY USB as have taken down my veras.
Hello @rafale77 , I have G550-35-1.7.4061.bin, mt7621s_Luup_ui7-1.7.5187-en-mios.squashfs and newmios-hooks.sh files. Can you tell me how can I use these files for recovery? There is no a clear tutorial about it. Is it possible to tell us how can you recover your vera plus with TFTP ? I want to apply the same stages to my vera secure. Thanks.
-
Is it means you use vera3_recovery_tool for recovery not TFTP? If it is yes, vera3_recovery_tool does not works at vera secure for me.
-
Under the hood, the recovery tool is using TFTP... I just used it and didn't really bother to inquire deeper as to how one would reproduce what it does.
And as far as I know it should work for the vera secure as well (I tested on both the plus and the edge) since all three are based on the same platform. I just don't have a firmware image for the secure.
-
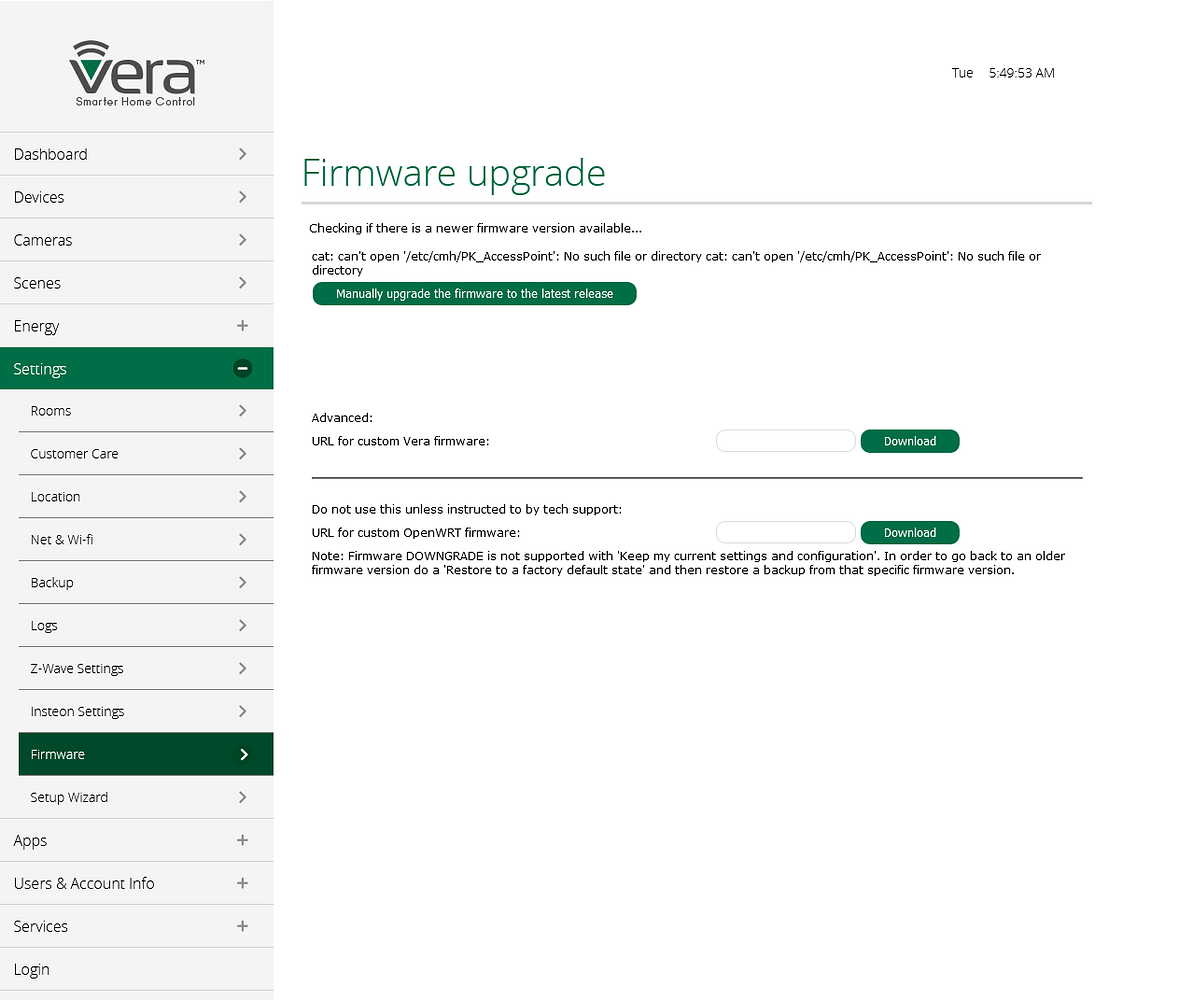
Thanks @rafale77. After using that tool, i still have the warning at the firmware upgrade page.
cat: can't open "etc/cmh/PK_AccessPoint' No such file or directory cat: can't open "etc/cmh/PK_AccessPoint' No such file or directory. Manually upgrade the firmware to the latest release.Do you have any idea about that warning?
-
Yes, This file may not be present in the image you just uploaded to the vera and is unique to each unit. It contains the unique ID which is used by the vera cloud server to identify vera units and normally is retained between firmware upgrades. If you can SSH into you unit, you can create a new file there and/or ask for support to give you that ID for your unit. I don't remember having had this problem myself except when I created my vera emulator in a virtual machine.
It is also that I ran my unit entirely "off the grid" for many years and never cared for the cloud service. If all you are trying to do is to run a firmware update, a dummy number in that file may be enough. You may also find that number somewhere in the logs uploaded in the vera cloud if you can find those.
-
The value is also written to NVRAM and may be still be there. Try:
nvram get serial_no -
@rafale77 and @toggledbits ,thanks both of you for this wonderful informations. What should I get when returning this
nvram get serial_nocode? I already have another (new unit) tried that code but no return any output. Maybe tomorrow I will need to ask support for that file -
You should be getting the serial number of your unit which should also be the content of your missing file.
You can then just create that file and insert that serial number in it using a text editor. I believe the vera only has "vi" installed but I had installed "nano" on mine which I vastly prefer. -
I will ask support tomorrow I hope I get a positive feedback.
-
If the serial number is on the label of the unit, all you need to do is create the file with that number in it.
If you scratch it down on a piece of paper, do this to avoid the editor:
cat >/etc/cmh/PK_AccessPointThat will just sit there doing nothing waiting for you to type. Type in, carefully the serial number from the label, then hit ENTER once, then hit CTRL-D once. You should get the shell prompt again. You can then confirm the file exists and has the right content.
-
Thank you @toggledbits . I will try your advice tomorrow and see the result.
-
-
-
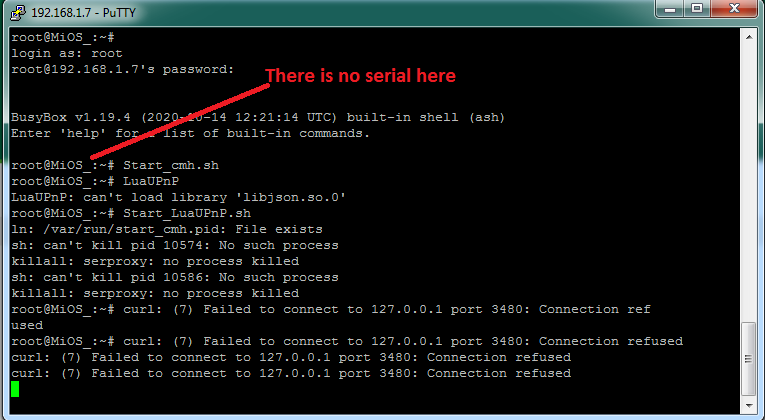
The error from your screenshot is pretty explicit... You are missing the libjson library for some reason. It looks like your firmware image was incomplete and was missing a lot of stuff.
run
opkg update opkg install libjsonYou likely will have other errors and will have to complete installation of dependencies.

 Video: Recover Bricked Vera plus
Video: Recover Bricked Vera plus